Threat Intelligence Platform on Cyber Domain
Threat Intelligence Platform applied to the cyber domain that aligns indicators with the Kill Chain; contrast, classify, and assign a criticality level, enrich and contextualize the internal observables with multiple information sources, categorizing and prioritizing threat and adversary hunt. Generated deliverables are for various audiences either strategic, tactical, or operative. Augurio Cyber Threat Intelligence Platform is the technological component that integrates all intelligence sources in both the public and the private cloud including Augurio NSA®, Augurio EP®, and Augurio X.®.
Technological components that integrate it:
- Augurio NSA®
- Augurio EP®
- Augurio X®

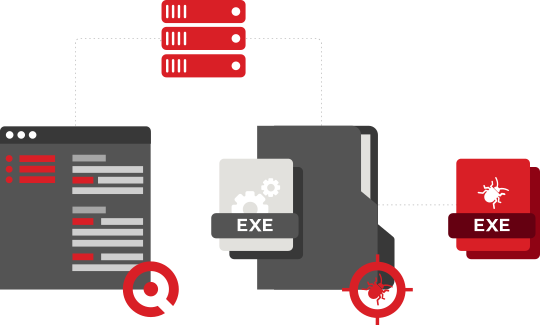
Solution that exploits malware in search of Adversaries
Solution that exploits malware analyzing executable files, office documents, compress files, Javascripts, Android among others in search for adversaries. Augurio Cyber Threat Intelligence Platform Is responsible for in-depth analysis both static and dynamic corroborating that the files doesn’t contain malicious artifacts that can compromise the organization.
Built-in component that detonates and provide intelligence for: Augurio CTI
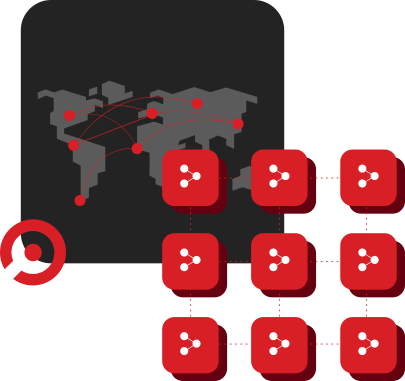
Security monitoring and analytics solution in Cyber Threat Intelligence Platform
Security monitoring and analytics network solution in Augurio Cyber Threat Intelligence Platform that collects and analyze multiple information sources including IP flows, packets, metadata, advance metadata, session and transactional data that contrast against indicators and cyber threat intelligence to discover, detect, and respond against adversaries. It is the technological component of network analysis that provides intelligence for Augurio CTI. Augurio NSA communicates with Augurio CTI via encrypted communication forwarding indicators and monitorization regarding the health of the network in a centralized way
Built-in component that detonates and provide intelligence for: Augurio CTI
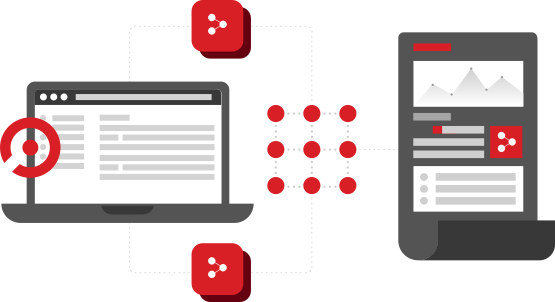
Analyze in-depth processes.
Endpoint solution that analyze in-depth processes, memory, registry, file system and logs within the system both client and server of Augurio Cyber Threat Intelligence Platform.
Augurio EP is used to priorize the response and detect adversaries’ activity and anomalies that adjusts to the tactics, techniques and procedures of the attacker in the Windows, Linux and Mac OS operating system. It is the technological component for detection and response in the endpoint that provides intelligence to Augurio CTI.